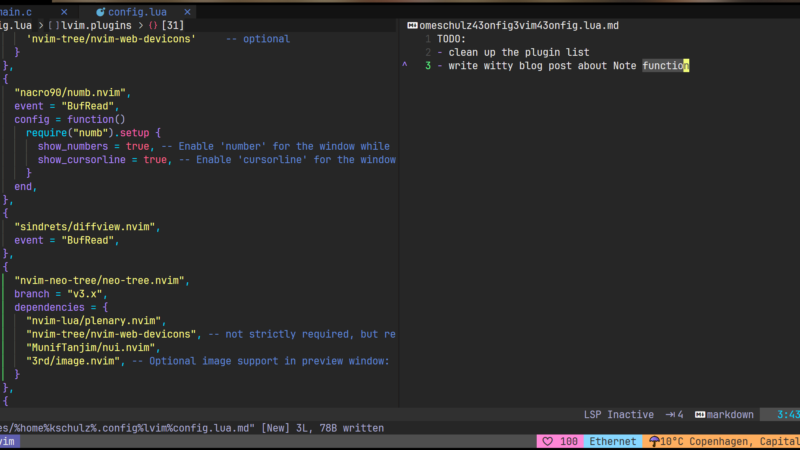
A quick look at 7-line piece of neovim lua code that has changed my workflow quite a bit. Note-taking simplicity at its best.
2024
01
Feb

Unveiling the Evolution: A Historical Journey through Computer Viruses
Exploring the evolution of computer viruses from the 1970s to present times, where I discuss the continuous battle between ever-evolving cyber threats and advancing cybersecurity. From pioneering malware like Creeper and Brain to the widespread destruction caused by I Love You and SQL Slammer, each era demonstrates escalating sophistication and societal impact, emphasizing the need for proactive security measures, education, and global collaboration to combat and adapt to these persistent cyber threats.
2023
23
May

Python virus for fun and profit
Can you write a self-replicating virus in python? I gave it a try.
2022
24
Nov

Better mobile privacy via FOSS
Android is great but from a privacy perspective there is a lot to be desired.
At least some of it can be fixed by installing FOSS (Free & Open Source Software) alternatives to common apps. Here I have assembled some of my favorites – Enjoy!
26
Jan

CVE-2021-4034 – my PoC for PwnKit
I made a Proof of Concept exploit (two actually) for the new Polkit CVE posted yesterday. Find a description and code here.
26
Jan
Using ctrl-z to toggle process in fg/bg
This is just a simple trick to get ctrl-z in bash to toggle a process between foreground and background.
A small but useful idea.
2021
25
Oct
Using core dumps for Linux privilege Escalation
A new vulnerability has been discovered that makes it possible to get a privilegded process to core dump in a restricted area.
This can via a few nifty tricks be abused to gain root access to a linux system
01
Sep
Hacking for a job (or just for fun)
The cyber crime unit of the Danish police has put out a boot2root box to find relevant applicants for a job as web specialist.
I could not resit trying it out.
21
Jun

Free world-wide Wifi for all IPhones (or how to trash the IPhone wifi settings)
What happens if you put a funky format string as SSID for your wifi AP? For IPhones it can have an unexpected outcome.
04
Jun

Who shares private social security number online?!?!
Have you ever shared a picture of your Danish social security card (in Danish: sundhedskortet) online? Maybe with a finger across to cover the secret number?
Think you’re safe from identify theft? probably not!